12 Virus Protection Best Practices for SAP Systems
Mar 9, '22 by Joerg Schneider-Simon
It’s smart for IT leaders to stay updated on virus protection best practices.
But just as most anti-virus solutions fail to protect SAP, many lists of virus protection best practices completely neglect SAP cybersecurity, even though SAP software stores and processes a wide range of sensitive and valuable information (personal data, financial data, product procedures, and intellectual property).
If you use SAP, make sure your protection measures include these 12 ways to protect this mission-critical system.
Best Practices for Protecting Your SAP Infrastructure
We’ll start at the foundation, which is your infrastructure.
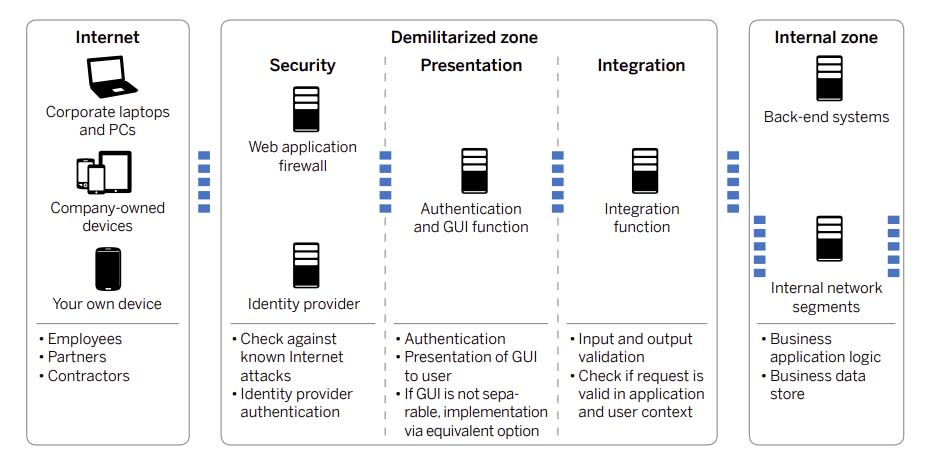
Best Practice 1: Divide your network infrastructure into zones
Prevent hackers who penetrate one part of your network from moving laterally into other areas of your network. Do this by dividing your network infrastructure into three zones, as illustrated in this diagram from SAP. As you can see, you must keep your back-end systems and in-house network segments separate from the upstream demilitarized zone and the internet in the internal zone.
Best Practice 2: Authenticate and verify all access between zones
Allow only essential connections to pass through the firewalls that separate each zone. Authenticate and verify all access through the internet within the demilitarized zone before it is forwarded to internal parts of the network. Do this with web application firewalls and authentication of identity providers. Also, restrict administrator access and ensure it is only facilitated using authenticated and encrypted connections.
Best Practice 3: Lock down your SAP database
Protect your data by restricting use of your SAP database, proprietary database applications and database-specific functions, as well as by managing authorization controls. Track all administrator access to the operating system. Use only accounts that are tied to individuals (not generic accounts that are shared by multiple people). When switching to administrative accounts, log all activities performed so that you maintain transparency.
Best Practice 4: Define a security strategy for personal devices
Hackers are well aware that many enterprises allow their employees to bring their own devices to work. Therefore, you must define a security strategy that differentiates between company-owned devices and personal devices.
First, document the process for secure software distribution, management, and configuration of these BYOD end points. Encrypt company data on these devices. Ensure that rules for password complexity for personal devices are as strict as they are for company devices. And use a centralized mobile-device management tool that lets you delete sensitive data on personal mobile devices.
Best Practices for Securing Your SAP Code
Hackers are always looking for new ways to exploit vulnerabilities in SAP code. Which means you must ensure that your code is always secure and up to date.
Best Practice 5: Implement SAP Security Notes Immediately
On the second Tuesday of every month, SAP publishes their latest security corrections and security recommendations in the form of patches that SAP calls Security Notes.
Establish a dedicated process for implementing these updates as quickly as possible. Hackers love organizations that are slow to patch newly discovered vulnerabilities.
Best Practice 6: Scan your custom code
When writing custom code, identify the most common vulnerabilities in your source code using source-code scanning tools. Ensure that your developers write their code in accordance with published data-protection regulations and compliance guidelines.
Best Practices for Your SAP Configurations
Your SAP systems are only as secure as their configurations. Poorly configured systems leave you vulnerable to attack.
Best Practice 7: Follow SAP’s recommended security settings
Follow SAP’s guidelines for securing your configuration. You’ll find them in SAP’s security baseline template, as well as in their latest white papers that deal with secure configurations.
Best Practice 8: Configure SAP to scan file uploads for viruses
Configure the SAP NetWeaver Virus Scan Interface (VSI) that’s found in every SAP application server to reroute file uploads through an SAP-certified virus scanner and content security solutions before loading them into the SAP software system.
Best Practices for SAP Operations
Protecting your SAP systems against viruses involves monitoring user access and authorization as well as logging any attempts by users to violate security.
Best Practice 9: Limit user rights
Do not give users rights that they do not need. And only give administrators the rights required for their respective area of work. Avoid granting authorizations that are not explicitly required. Limiting user rights prevents standard accounts that become infected with viruses from infecting vital systems that require administrator access.
Best Practice 10: Do not use standard profiles for RFC
Never use standard user profiles for Remote Function Call (RFC) connections and background jobs. RFC attacks penetrate test systems and then move to production systems by exploiting the privileges of RFC users in client systems. So, restrict authorizations by giving technical users only the minimal authorization they need.
Best Practices for SAP Security Compliance
Your success at protecting your SAP systems against viruses and malware depends on your level of vigilance. Being vigilant means regularly reviewing your security posture to ensure that you are compliant.
Best Practice 11: Conduct regular security audits
Regularly conduct audits to detect irregularities, vulnerabilities and attacks. Make these audits part of a comprehensive corporate audit plan that you update at least once a year.
Best Practice 12: Prepare for emergencies with a robust backup process
Naturally, your goal is to follow these best practices to deter viruses and malware. But in the event that your SAP systems do manage to get infected, you need a way to recover your data.
You can only do this if you have backed up your data: Implement a comprehensive data backup process that protects your enterprise in the event of the infection of one server or database, right up to the compromise of an entire data center.
Best Practices for Protected SAP Systems
SAP applications, databases and systems remain attractive targets to hackers because they contain valuable data. To protect your enterprise, you must follow the latest virus protection best practices for SAP systems.
Which raises a rather delicate question: Just how prepared is your organization to withstand a virus attack? Our helpful cybersecurity self-assessment helps you determine whether your SAP system is well-secured, or low-hanging fruit for attackers.

Share this on social: