Cybersecurity for SAP Managers: Directory Traversal Attacks
May 9, '17 by Joerg Schneider-Simon
Directory traversals are one of the most common SAP cybersecurity attacks, accounting for 20% of the security notes published by SAP. In these attacks, cybercriminals gain unwanted access to sensitive files or system directories, potentially resulting in a complete system compromise.
This post is the fourth in an ongoing series to educate SAP managers about common cybersecurity threats. Previous posts have covered such major threats as denial of service (DoS) attacks, injection attacks and cross-site scripting (XSS). Today, we’re focusing on the widespread damage directory traversal attacks can wreak on SAP systems – and how to protect against them.
Understanding Directory Traversal Attacks
SAP directory traversal attacks occur when a cybercriminal manipulates input to the SAP application in a way that grants them access to forbidden directories on the application server beyond the application context. The attacker may then be able to launch commands and access information outside the server’s application directory, gaining access to critical system configuration files and back-end systems.
To launch a directory traversal attack, a cybercriminal simply needs a browser and a general understanding of where to find files and directories on a target web server or web application. By submitting a parameter with one or multiple “../” in the file path to a vulnerable application, the attacker can access virtually any directory in the server’s file system. With just a little trial and error, he can quickly figure out how many “../” sequences he must use in the file path to access sensitive resources.
In an SAP system, although the web servers themselves aren’t vulnerable, many application components are – especially in custom code. Let’s look at the two common types of SAP system directory traversal attacks.
Application-Based Attacks
In this type of attack, cybercriminals try to submit a targeted parameter to a vulnerable web-based application, hoping to retrieve files outside the application’s boundaries. Attackers might try to retrieve protected files in two ways: absolute and relative path traversals.
Consider a web-based application that includes this static HTML file in the output:
http://www.myserver.com/webapp?ViewFile=motd.html
- In an absolute path traversal attack, the cybercriminal would include the full path to a specific file, i.e. the standard UNIX user/password file:
http://www.myserver.com/webapp?ViewFile=/etc/passwd
- In a relative path traversal attack, the attacker would identify the file relative to the application’s directory on the server in order to gain access to sensitive information:
http://www.myserver.com/webapp?ViewFile=../../../etc/passwd
SAPCAR Archive Formats
In comparison, SAPCAR, SAP’s compress utility, is a complex archive file format that’s also vulnerable to directory traversals. Unlike its ZIP file counterpart, which traditional virus scanners can scan to identify and prevent directory traversal attacks, SAPCAR is a proprietary solution that isn’t scannable by out-of-the-box antivirus products.
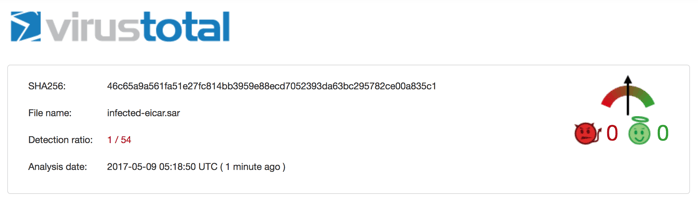
Also, unlike many other archive formats, SAPCAR allows absolute paths to be stored in the archive. It also allows the storing of files in the archive that will be restored at absolute or relative positions higher than the current work directory.
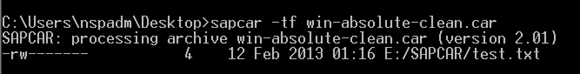
A hacker can create easily create a malicious SAPCAR archive — such as one including a critical SAP server configuration file — designed to compromise your SAP system’s security. When an unsuspecting user restores or extracts the altered files, the files are saved to the same location as the path stored in the archive. If the user has the right access permissions, unpacking the archive could be disastrous.
Consequences of Directory Traversals
Directory traversal attacks can have significant effects on entire SAP systems, including:
- Overwriting critical operating system binaries
- Exposing confidential data and allowing for its modification
- Compromising applications and/or underlying operating systems
- Rewriting static HTML content
- Allowing attackers to intercept login credentials and keystrokes overwrite data, impersonate users and enable arbitrary file uploads
- Inserting new administrator accounts
- Modifying system startup settings to weaken or disable system security
In the worst-case scenarios, directory traversals can result in full-system compromises and may render servers unusable. For the SAP systems that manage critical business processes, these breaches could be devastating.
How to Prevent Directory Traversal Attacks
Because customized SAP applications can often have multiple directory traversal vulnerabilities, it’s important for SAP managers to take a proactive approach by ensuring your systems:
- Filter out user input to prevent malicious content from being submitted to the application
- Have in place the relevant security checks for path traversals.
- Protect against exploitable programming errors.
- Constrain file access functionality to a list of allowed files and paths not based on user input.
- Restrict public access to certain portions of the server’s file system.
While these are ways to start bolstering security, a comprehensive SAP content-security system is critical to help protect against the devastating effect a breach of confidential information can have on your organization.
Traditional virus scanners can’t protect your SAP system from directory traversal attacks, but bowbridge's solutions can. Contact us today to learn more.


Share this on social: