Macro Malware and “Secure” Documents: What You Need to Know
Jan 25, '17 by Joerg Schneider-Simon
Many users safely employ macros to streamline repetitive processes. Unfortunately, many cybercriminals also use macros to hide malicious code in an attempt to steal information or money.
After several quiet years, macro malware is experiencing a comeback, which may put the integrity of your business’s SAP application and data at risk.
To protect your infrastructure against these content-based attacks, it’s important to understand the nature of macro malware, the types of documents they hide in, and the steps you can take to minimize your exposure.
What Is Macro Malware?
Macros are simply sets of commands or actions that help users automate tasks. Most commonly, macros are used in Microsoft Office documents (like Word or Excel) as a shortcut to launch certain repetitive actions, such as formatting text a certain way. Depending on the task, macros can save users hours of time.
Macros can be used to automate literally any series of keystrokes. Therein lies their beauty – and their danger: Hackers can program macros to run malicious software on an unsuspecting victim’s computer.
To spread the malware, a Microsoft Office document containing the macro malware is uploaded into an SAP application from an outside point of entry, such as an external PC or mobile device. Depending on the application or workflow, the file may be synchronized onto a corporate endpoint or retrieved by a user. When the file is opened, the macro automatically launches – with the potential to wreak all sorts of harm almost immediately.
While a highly aware IT staff member may know better than to open an outside file without scanning it first, many employees — for example, shipping clerks, technical support staff and human resources personnel — routinely open such documents as part of their normal work processes without giving it a second thought.
It’s critical, therefore, that appropriate measures be put in place to scan as many of these documents as possible before they are stored within an SAP database or opened within the system, to prevent the macro from being unleashed.
Where Can Macro Malware Appear?
Cybercriminals embed their macro malware in seemingly standard, nonsuspicious documents. These files may then be directly uploaded to any number of SAP applications, including:
- SAP E-Recruiting, by job seekers uploading CVs, resumes and cover letters as Microsoft Word files.
- SAP Supplier Lifecycle Management, when vendors upload spreadsheets and/or detailed quotes as Microsoft Word or Excel files.
- SAP CRM, by users uploading or updating documents from unsecured devices outside the company network, including home computers, mobile devices and tablets.
- SAP Mobile Documents, when outside users upload, synchronize and exchange any number of file types, including Microsoft Office documents.
Increasingly sophisticated text and images give users a false sense of confidence when asked to open the innocent-looking document. This provides criminals with the perfect delivery mechanism to cause crippling damage in the blink of an eye.
“Secure File” Macro Attacks
One of the latest trends in macro-based malware is to trick the user into activating the macro in order to access “secured” content in the document. In these cases, upon opening the corrupted file, a warning sign appears asking the user to enable the content to view the document. Of course, enabling the content automatically launches the macro.
Stu Sjouwerman at the KnowBe4 blog recently shared several examples of these warnings – and they’re alarmingly well done:
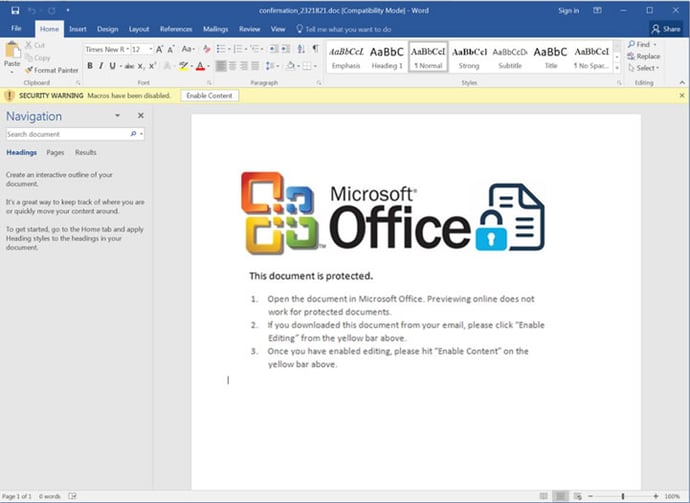
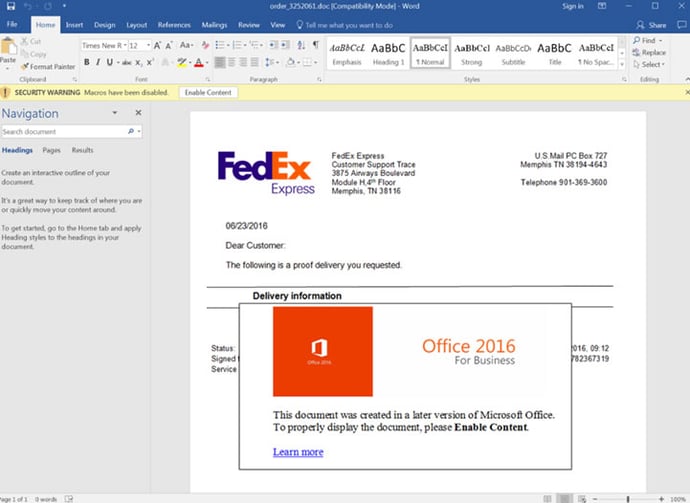
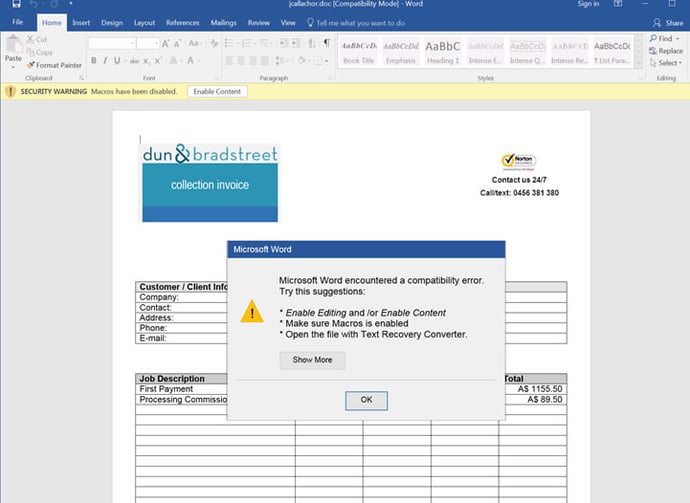
To an unsavvy user, these warning screens look authentic, and many employees will automatically do as the screen asks.
For example, imagine Mary in Human Resources must screen resumes that applicants have uploaded into SAP E-Recruiting. Upon opening a resume in Word, she sees a message that looks native to Microsoft Office. The message states that personally identifiable information in the resume is protected by something called “Microsoft Office Advanced Document Security Feature” (which doesn’t actually exist and was made up by the hacker). To view the content, the screen asks her to click Edit, then Enable Content.
Mary doesn’t think anything looks suspicious; after all, Microsoft always seems to warn her about something. So with the best of intentions, she clicks the buttons — and launches the malware that jeopardizes the entire SAP system.
That mistake can be catastrophic, and unfortunately, Mary isn’t alone in her naivete.
It’s likely that the ability to accept and open uploaded documents within your SAP system is important to your business. However, as demonstrated above, this also means you’re at risk of an employee accidentally running a malicious macro.
So, what’s the solution?
Standard SAP Protocols Aren’t Enough
You can’t count that filtering and blocking content uploads by file extension will offer the full extent of protection you need. Malware developers are always one step ahead, modifying file extensions to circumvent security features and hide malware, which leaves your system still vulnerable.
Fortunately, there are simple steps you can take to help employees safely do their jobs while still laying a foundation for security:
- Activate the macro security function on Microsoft Word and Excel.
- Educate your users to never click links, enable content or macros, or run programs unless there is absolutely no question about security. Most malicious payloads can’t execute without user interaction.
- Ensure that all PCs are running current software versions and all security patches are installed.
- Employ a security strategy that can detect new and unknown malware.
These steps are a good start, but more advanced companies will want to do more to protect business-critical IT assets, such as SAP applications.
Using a Multilayered Security Approach
Implementing the bowbridge Anti-Virus solution lets you add layers of protection to your SAP application infrastructure. As the only SAP-certified product to protect against malware, bowbridge Anti-Virus lets you:
- Ensure content and extensions match. Hackers can no longer easily disguise embedded macros by simply changing file extensions. The bowbridge solution checks for file format consistency, ensuring data integrity.
- Block all macros. Knowing that all macros are blocked for users who don’t need them allows you to upload and download files with confidence.
- Detect and block malicious macros. Is using macros essential for your business? You can still do so safely. The bowbridge Anti-Virus solution detects and blocks malicious macros with integrated, industry-leading virus scanning engines from McAfee and Sophos.
Focusing exclusively on SAP security, bowbridge can help protect your business against the latest malware threats. Contact us to learn more about how the bowbridge Anti-Virus solution can protect your SAP system.


Share this on social: