SAP Cyberattacks: How Prepared Are You?
Aug 19, '20 by Joerg Schneider-Simon
Why do so many organizations use SAP software? Because it gives them powerful access to their data and mission-critical processes.
Unfortunately, that’s also why SAP is such a choice target for cyberattack.
If your organization uses SAP software for mission-critical functions, then hackers likely have you in their crosshairs (or they soon will). Which brings up a rather pressing question. How prepared, exactly, is your organization for an SAP cyberattack?
To answer that question, you must change the way you think about cyberattacks on SAP systems.
Think Like a Disgruntled Employee
If your SAP systems are internal only, and not connected to the Internet, you likely believe that you don’t have to worry about outside attackers.
But you’d be mistaken.
A whopping 34% of data breaches involve internal actors—typically disgruntled employees. Insider threats are real when it comes to your mission-critical systems. Think of the harm that can be done by one disgruntled employee, one dishonest contractor or even a targeted attack, where a seemingly innocent visitor plugs a device into a hidden network socket in your office.
To prepare yourself against an SAP cyberattack, you should view your internal network the way you view the Internet—not trustworthy. With the erosion of network perimeters and the proliferation of mobile and roaming devices moving in and out of the corporate network, it is increasingly difficult for large organizations to segregate trusted from untrusted networks.
One compromised employee laptop or smartphone is enough for an attacker to bridge into your network. So, apply a zero-trust mindset to your mission-critical systems—like your SAP systems—and then to outside networks.
Think Like a Hacker
Another way to measure your level of preparedness for an SAP cyberattack is to think the way hackers think. And that means avoiding one of the big myths of cybersecurity.
Some folks still believe that while mission-critical systems need to be hardened against attacks, less critical systems don’t. For example, they believe that because only their production system contains critical data, that’s the only system that needs to be secured against cyberattacks.
But as soon as you start thinking like a hacker, you see the folly of believing this myth. Hackers know that less critical (and less secure) systems are an effective gateway to more-secure, mission-critical systems.
SAP systems are interconnected. So, if you are a hacker, why waste time, money and resources attacking the most locked-down, secure and audited production system when you can instead gain access to that very same system by attacking an adjacent—and less secure—system?
This is what hackers do. They compromise QA, development, and other less-secure systems, and then move laterally to escalate their privilege to the production system. They gain access to more-secure systems by exploiting shared passwords, by RFC-pivoting, and by exploiting shared OS-level vulnerabilities.
Remember, attackers prefer to break through the weakest door first. So, apply your security protocols to all SAP systems, regardless of whether they are production or not.
Think Like Google
What do you suppose is the best tool for identifying SAP systems that are exposed to the internet? Is it a dedicated search tool like Metasploit and Shodan? Or just plain old Google?
The answer is Google. Or, to be more precise, Google Advanced Search.
Many SAP systems expose the full application URL to the Internet. Instructing Google to search for splash pages or login pages with certain patterns in the URL reveals tens of thousands of SAP systems… with zero effort. Advanced searches and combinations of search terms helps attackers narrow-down their target list.
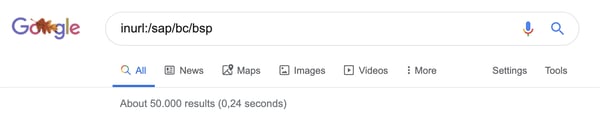
A search for SAP Application Servers, for example, returns a whopping 50,000 results.
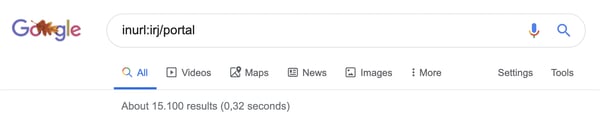
A search for SAP NetWeaver Portal Servers returns 15,000 results.
To prevent hackers from finding your Internet-connected SAP systems through Google, use a tool that both re-writes URLs to hide any reference to SAP applications in external-facing URLs, and re-writes links within the HTML of web-facing SAP applications.
Advanced web application firewalls will do this for you. Or you can use bowbridge Secure Web Dispatcher for SAP applications (targeted for release in Q3/2020) to perform these translations.
How prepared are you for an SAP cyberattack? If you have read this far, you are better prepared than you were a few minutes ago. Now that you are thinking like a disgruntled employee, a hacker and the world’s most popular search engine, you are better prepared to secure your SAP systems against cyberattacks.
To test your preparedness even further, take our self-assessment quiz.


Share this on social: