ERP Systems at Risk: Top 5 Takeaways from the Onapsis/Digital Shadows Report
Aug 9, '18 by Joerg Schneider-Simon
On July 25th, the world received some startling news: The US Department of Homeland Security had issued an alert about ERP systems (specifically, SAP and Oracle) being targeted by nation-state attackers, cybercriminals, and hacktivist groups.
This alert was based upon a research report, ERP Applications Under Fire: How cyberattackers target the crown jewels, issued by Onapsis and digital risk management firm, Digital Shadows. In their research, they have uncovered some alarming news affecting the hundreds of thousands of ERP implementations around the world.
We reviewed this report, but also had a discussion with Juan Pablo Perez-Etchegoyen, CTO of Onapsis, who among other roles, is responsible for the SAP cyber-security research that has made Onapsis Research Labs an ultimate authority on the topic. Here are our takeaways:
Takeaway #1: ERP Cybersecurity Has Flown Under the Radar
When discussing ERP security, two types of security come to mind: cybersecurity, and security as it pertains to user access and authorizations such as users, roles, profiles and permissions. Unfortunately, most companies have only focused on the latter, leaving cyber-security sorely neglected.
By doing so, they’re exposing themselves to an enormous level of risk.
“For most companies, their ERP has a direct link to their critical infrastructure: payroll, HR, vendors, customers, manufacturing, logistics. If their ERP is not running, they cannot operate and could lose millions of dollars every minute. Plus, data from ERP systems is integrated across other platforms and business processes,” says Perez-Etchegoyen.
At first glance, it’s a baffling issue. Why have companies left such a business-critical set of applications so vulnerable? The report makes it clear that a number of factors have made it difficult for organizations to stay up to date with their ERP cybersecurity:
- Complex system architectures
- Customized functionalities
- High number of interfaces and integrations
- Proprietary protocols
- Detailed and fine-grained access controls
- No tolerance for unplanned downtime due to supported processes
- Lack of knowledge and processes for ERP security
In short, because ERP is both complex AND important, organizations have adopted an unofficial policy of slightly fearful neglect, where they avoid even basic updates and security patches out of concern that they’ll make a mistake and “break” something.
Takeaway #2: Interest in Cyberattacks on ERP Systems Is Increasing
The data has spoken: The interest among hackers in exploiting ERP vulnerabilities has skyrocketed.
Using threat intelligence, the report charted the number of mentions of specific ERP vulnerabilities over social media, forums, the dark web, criminal sites, and more. Onapsis and Digital Shadows observed a 160 percent increase in the activity and interest around ERP-specific vulnerabilities from 2016 to 2017. The chart found on page 12 of the report makes it clear that cyberattackers are increasingly realizing the wealth of opportunity presented by such a vital — and vulnerable — system.
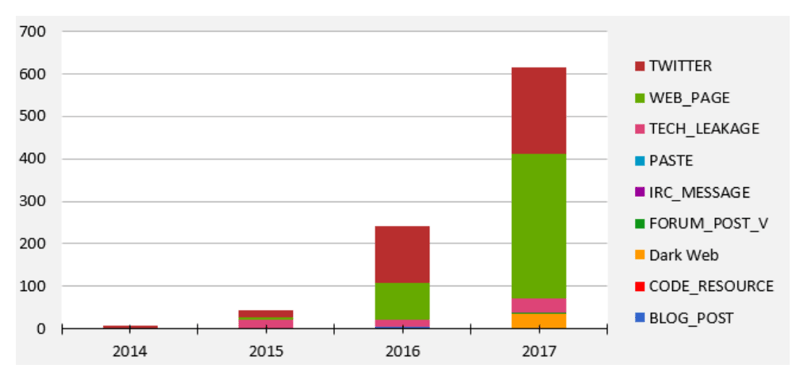 Graph: Mentions of SAP Common Vulnerabilities and Exposures with Publicly-Available Exploits
Graph: Mentions of SAP Common Vulnerabilities and Exposures with Publicly-Available Exploits
Takeaway #3: Everything’s on the Internet … And Probably Shouldn’t Be
One of the main benefits of an ERP system is that it allows multiple parties to share data and files. An accounts payable clerk in Chicago can quickly share an invoice and work order with a payment processing department in Stockholm. However, this requires connecting over the internet.
Internet connectivity is not necessarily a risk, but when combined with the aforementioned lack of ERP cybersecurity, major problems can develop. The report highlighted how cybercriminals are using Google to detect internet-connected ERP applications that are vulnerable. In some cases, these applications are no longer maintained and patches are not available — yet, they’re still live: a forgotten but completely open passageway into the organization’s SAP system.
In other cases, insecure deployments are the problem, with applications being blithely connected to the internet without restricted access or strict firewall configuration.
“There is a huge number of internet-facing ERP applications,” says Perez-Etchegoyen. Companies need to make sure those are properly taken care of and should also ask themselves if those applications need to be internet-exposed in the first place.
Takeaway #4: People Are a Problem
Even with the best technical cybersecurity for an organization’s ERP system, there is still another major risk factor: human carelessness.
The report found that multiple examples of organizations being exposed by their own employees or by third parties. In one memorable instance, SAP contractors were sharing login credentials on Trello. In many cases, third-parties’ public facing file repositories contained files that exposed sensitive technical information.
With third parties, enforcement can get tricky. It’s one thing to set up processes and corrections with your own people, but what if a supplier’s cybersecurity is lax?
“It’s important to prioritize all of these moving parts,” explains Perez-Etchegoyen. “Have conversations with these third parties to cover all the endpoints. You can’t control what they do, but you should at least analyze and have a full understanding of the risk, so that you can make conscious decisions on how to handle them.”
Takeaway #5: There’s a Lot You Can — and Should — Do
ERP applications are vital to the operation of a business. They are also vulnerable to attack and are an increasingly popular target.
With that in mind, how can organizations protect themselves?
Here are the report’s recommendations:
- Identify and mitigate ERP application layer vulnerabilities, insecure configurations, and excessive user privileges: Assess vulnerabilities, assess system configuration, review privileges regularly, and implement processes to eliminate cybersecurity gaps.
- Identify and remove dangerous interfaces and APIs between the different ERP applications in the organization, especially those with third parties and that are internet-facing: Map existing interfaces and APIs and assess their configuration. Review internet-facing applications and only expose those that are truly necessary.
- Monitor and respond to sensitive ERP user activity and ERP-specific indicators of compromise: Monitor for suspicious user behavior and signs of compromise. Incorporate ERP monitoring into existing processes.
- Monitor for leaked ERP data and user credentials: Monitor threat intelligence for compromised credentials, any exposed information, and any applicable exploits or vulnerabilities.
The key is to come at SAP cybersecurity from all angles, says Perez-Etchegoyen: “Applying patches isn’t enough. A firewall isn’t enough. Protection has to be multifaceted and has to be applied across the entire ERP application platform for it to be effective.”
And where do vendor solutions, like bowbridge’s, fit into the picture?
“Vendor solutions provide extra security to ERP Applications in different layers. Organizations will have to start adopting these types of solutions to make sure their cybersecurity is comprehensive and holistic.”
Fortunately, many organizations are already reducing their risk. Cybersecurity may be a never-ending arms race, but with increased awareness comes increased protection, helping more and more companies stay on top of their ERP cybersecurity and running at full speed.
To download the report, click here.


Share this on social: