Six Steps to Improve SAP FIORI Security
Jun 14, '23 by Joerg Schneider-Simon
Hackers have been quick to notice that many SAP applications, servers, and databases that were once hidden behind corporate firewalls are now exposed to the web, making them prime targets for attacks.
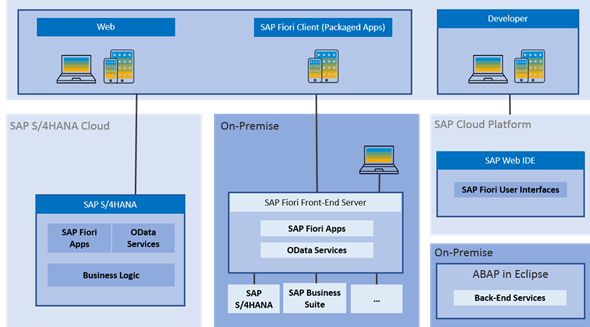
One common denominator in this push to the web is SAP FIORI, the design language and user experience approach that SAP developed for itself, its customers, and its partners to use in their business applications.
Applications that use the SAP FIORI design language include SAP S/4HANA and SAP C/4HANA suites, SAP Analytics Cloud, SAP Data Hub and SAP Ariba. The goal of SAP FIORI is to give designers and developers a set of tools and guidelines for quickly creating apps for any platform.
 (source)
(source)
SAP FIORI exposes enterprises to increased security risks primarily because it increases the attack surface. How? By exposing previously isolated, on-premises SAP systems to the public internet and mobile networks — attackers now have many more points of vulnerability, in the form of SAP FIORI interfaces, to attack.
Attack attempts may be inevitable, but successful attacks are not.
We spoke with Christoph Nagy, CEO of SecurityBridge, to get his thoughts on where SAP FIORI security stands today. SecurityBridge is a comprehensive platform covering SAP threat detection, vulnerability management, custom code scanning, and patch management.
Here are six ways to improve your SAP FIORI security.
1. Benchmark Your SAP Security Vulnerabilities
Take an inventory of all the ways that hackers can attack your SAP systems through SAP FIORI interfaces. Include all devices that operate both within your firewall and outside of it. Pay particular attention to mobile devices, such as tablets and phones.
“From our experience as a platform provider for cybersecurity in the SAP field, we see that a lot of attacks are starting from the inside,” says Nagy. “Inside doesn't always mean an employee with malicious intent. It can be an employee who is a victim of social engineering. It can be a USB stick that an employee finds in the company parking lot. It can be an employee getting a call, supposedly from the help desk, asking the employee to share their login credentials.”
2. Get the Security Basics Right
Make sure you are already using best practices for securing SAP systems against attacks, such as:
- running the latest releases of SAP applications.
- installing the latest SAP Security Notes (security patches) as soon as they are issued.
- not allowing users to share passwords.
- not permitting users to use weak passwords.

– Christoph Nagy, SecurityBridge
3. Harden Your SAP Infrastructure
Improve your defenses by hardening your SAP infrastructure.
Start with policies and then move on to the practical: Create administrative policies, processes, procedures, and guidelines that describe how to maintain security at administrative and technical levels. Set strict hardening policies and start monitoring compliance.
In particular, harden your gateway servers, message servers, and ICF components. Here are some steps to take:
- Erect a network firewall in front of your SAP Web Dispatcher limit network connectivity to required ports and protocols.
- Hackers aim to penetrate SAP FIORI connections to infiltrate backend SAP servers. Prevent these attacks with a Web Application firewall in front of your SAP Web Dispatcher that protects your backend servers against attacks that exploit this FIORI connector. Better yet, consider merging the functionalities of an SAP-specific WAF and the Web Dispatcher and use bowbridge Application Delivery Controller for SAP Solutions.
- Block access to the HTTP port on the NetWeaver Gateway server at the firewall.
- Implement HTTP Strict Transport Security.
- Allow access to critical FIORI apps only over Virtual Private Networks.
- Implement redirections from HTTP to HTTPS URLs in SAP Web Dispatcher and SAP Internet Communication Manager.
“We are seeing a shift from audit-driven security to continuous security,” says Nagy. “We need to look at vulnerability management, we need to look at the lock stack of SAP, which is a challenge by itself because it's more transaction-driven and business-driven than security-driven and patch management.”
4. Watch Your Connections
Your goal is to give attackers as few entry points into your SAP systems as possible, and to make those entry points secure.
Start by getting a grip on your access controls. Know who is using your SAP systems, why they are using them, when they are using them, and how they are accessing them. Then take the following steps:
- Deploy Security Assertion Markup Language (SAML), proxies strong authentication, such as two-factor authentication to deny access to unauthorized users.
- Encrypt your connections and your data using TLS and SNC. Encrypted connections protect your SAP data while in transit. And encrypted data makes your information useless if it falls into the hands of attackers.
“You need to think about security in every aspect of the feature set that you're going to implement,” says Nagy. “With Fiori, you can have access to native device capabilities. So, you can have a mobile phone, and a mobile phone has a camera. From the Fiori app, you can access the camera, you can access the photo library, and essentially gain access to privacy data on that device. So, you need to have the security, the data protection, the privacy aspect in mind if you develop for additional devices. That's certainly a challenge.”
5. Monitor Activity by Bad Actors
SAP FIORI Security is not a one-and-done activity. Hackers and cybercriminals never rest, so neither should you.
Monitor your SAP systems 24/7 for suspicious activity. This includes activity by your users, both standard and privileged. Whenever possible, feed security data into a SIEM solution or SAP Enterprise Threat Detection to identify threats at the infrastructure layer and the business logic layer.
Continuously monitor for violations of your security policies. When you find deviations, take action immediately to remediate threats and change user behavior.
“Now, with that information, with that trigger of being aware that a lot of recipe data, a lot of great secrets have just left the environment, you need then to take an educated decision on what you actually do as the next step in your response. You must stop the leakage if you are in time.”

– Christoph Nagy, SecurityBridge
6. Use Third-party SAP Security Tools
Standard OS-level antivirus programs do not recognize or address SAP cybersecurity threats. If you want to protect your SAP systems against viruses and content-based attacks, you must use security tools developed by other firms.
“SAP systems are subject to frequent changes,” says Nagy. “So, a business requirement can also mean that you need to change basis parameters and activate or deactivate services and other functionality. This has an impact on your security posture and needs to be continuously evaluated. It's about vulnerability monitoring that contains critical access management, that contains the security-relevant configuration and hardening. Knowing which security-relevant patches are missing for the technology stack that SAP customers are using is still a huge challenge.”
This is also true for SAP FIORI security. To protect against attacks, consider using third-party tools that are custom-built to protect the data that flows in and out of SAP applications. Application Delivery Controller by bowbridge, for example, ensures the availability, integrity and performance of web-exposed SAP applications for on-premises and cloud-based SAP implementations. This software is cloud-ready and built specifically for SAP applications, making it the market’s only software-based Application Delivery Controller for SAP applications.


Share this on social: