2017 in Review: SAP Security Notes
Jan 25, '18 by Joerg Schneider-Simon
ERP security has long been focused on operational issues, such as permissions and segregation of duties. That may no longer be enough to keep organizations safe.
2017 was filled with headlines about major data breaches and cyberattacks, and it’s likely to get worse: 89% of security experts anticipate more cyberattacks against ERP systems in the coming years – and 30% expect the increase to be significant.
To understand whether your company’s SAP cybersecurity is at risk, it’s helpful to look back at the past year to understand what happened, which vulnerabilities are most concerning, and how SAP is addressing them.
SAP Security Notes: The Big Picture
In 2017, SAP released 269 security note documents:
- 7 were Hot News
- 35 were High Priority
- 202 were Medium Priority
- 18 were Low Priority
Three of the Hot News security notes indicated major vulnerabilities to injection attacks, which is alarming as it can put sensitive data at risk.
| BC-DOC-RIT | 2371726 | Code Injection vulnerability in Text Conversion |
| BC-DOC-TER | 2357141 | OS Command Injection vulnerability in Report for Terminology Export |
| BC-TRX | 2419592 | Code Injection vulnerability in TREX / BWA |
A commonly detected vulnerability type was cross-site scripting (XSS), followed by SQL injections and directory traversal attacks. The other vulnerabilities were related primarily to missing authorization checks.
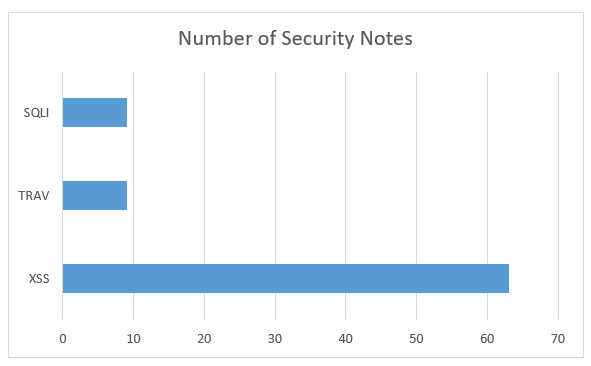
Cross-Site Scripting (63 Notes)
XSS remains the most widespread SAP vulnerability type, comprising 23% of all 2017 SAP security notes. As we’ve explained in more depth, XSS attacks involve malicious code injected into otherwise trusted websites or web-based applications, typically using JavaScript.
Out of the XSS-related notes in 2017, three were High Priority:
| BI-BIP-BIW | 2381071 | Cross-Site AJAX Requests vulnerability in SAP BusinessObjects |
| BI-RA-WBI-FE-HTM | 2396544 | Cross-Site Scripting (XSS) vulnerability in SAP BusinessObjects Web Intelligence HTML interface |
| BC-FES-ITS | 2318760 | Cross-Site Scripting (XSS) vulnerability in ITS / SAP GUI for HTML |
Note 2396544 is a particular one to mark. The note indicates “SAP BusinessObjects Web Intelligence HTML interface does not sufficiently encode user controlled inputs, resulting in Cross-Site Scripting (XSS) vulnerability.” In addition, the complexity of the attack is low, but has a high potential impact on data confidentiality.
SQL Injections (9 Notes)
SAP applications use SQL to retrieve or store records. This SQL is vulnerable to code injections that cyberattackers can use to access, manipulate, and even destroy critical records and data, giving them the opportunity to wreak massive amounts of damage.
For example, the high-priority note, 2319506, highlights an SQL injection vulnerability in database monitors for Oracle. Potential impacts of this vulnerability: reading/modification/deletion of sensitive data, unauthorized execution of commands, and even Denial of Service.
Directory Traversal Attacks (9 Notes)
Directory traversal attacks are common on SAP systems. They take place when a cybercriminal manipulates input to the SAP application in a way that grants them access to forbidden directories on the application server beyond the application context. The attacker may then be able to launch commands and access information outside the server’s application directory, gaining access to critical system configuration files and back-end systems.
But Wait … It Gets Worse
It is vital to remember that all SAP-originated security monitoring (and resultant security notes) are only applicable for standard installations of SAP.
However, most SAP installations are not standard. Instead, SAP installations are usually customized. This creates a potentially much larger number of vulnerabilities that SAP does not monitor and cannot address.
This is exacerbated when many companies put off reviewing security notes and installing patches, which further increases their exposure to cybersecurity risks.
But Wait … It Gets Better
SAP security notes provide helpful visibility into the fight against cyberattacks. However, they shouldn’t be the only tool in an IT or SAP team’s toolbox.
The best defense against an ever-changing field of cybersecurity threats is a solution that offers a comprehensive set of anti-virus and application security options designed specifically for SAP. Instead of waiting for security notes to be issued and eventually installing the necessary patches, the right solution will be updated as soon as new threats are discovered, resulting automatic, vigilant protection.
Want to know more about how to stay ahead of attackers and protect your SAP system? Watch our webinar, Protecting Your SAP Applications from Content-Based Cyberthreats.


Share this on social: