5 Cybersecurity Stats and What They Mean for SAP
May 21, '19 by Joerg Schneider-Simon
The news these days on cybersecurity is often grim. High-profile data breaches affect millions of consumers, data sabotage threatens vital infrastructure and systems, and massive phishing schemes wreak havoc on personal privacy. Cybersecurity professionals are the front lines in this new war and are fighting valiantly against an ever-growing horde of enemies.
But what about the professionals who work to keep SAP systems safe? What do the facts and figures around today’s state of cybersecurity mean for them? We examine five cybersecurity stats and what the implications are for SAP.
The average cost of cybercrime for an organization has increased to US$13 million. (Accenture/Ponemon)
What This Means for SAP Cybersecurity
With the average cost of a cybersecurity attack rising precipitously, organizations have a strong impetus to pinpoint any weak spots in their armor. One of these weak spots tends to be SAP cybersecurity. This is often because SAP cybersecurity does not cleanly line up within the responsibilities of either SAP managers or Information Security Managers. As such, SAP cybersecurity tends to fall through the cracks.

Source: https://www.accenture.com/_acnmedia/PDF-99/Accenture-Cost-Cyber-Crime-Infographic.pdf
The potentially extreme costs of a breach to an SAP system should be a wake-up call to organizations to put the proper time and resources into making sure clear roles and responsibilities are assigned.
Total malware samples have gone from 500M to over 800M in less than two years. (McAfee)
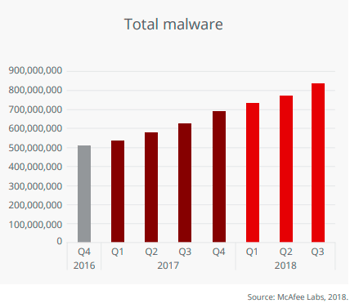 What This Means for SAP Cybersecurity
What This Means for SAP Cybersecurity
Because SAP applications store data in locations standard anti-virus cannot access, such as database volumes or external document management systems (DMS), they are unable to protect them. File-transfers in SAP applications therefore completely bypass such OS-level anti-virus solutions.
Combine that with the skyrocketing number and increasing sophistication of malware plus the growing number of highly targeted attacks, and it becomes clear that attacks on the crown jewels of business — data stored and processed in SAP applications — are likely to continue to grow in number and impact.
Microsoft Office formats such as Word, PowerPoint and Excel carry the most malicious file extensions at 38 percent of the total. (Cisco)
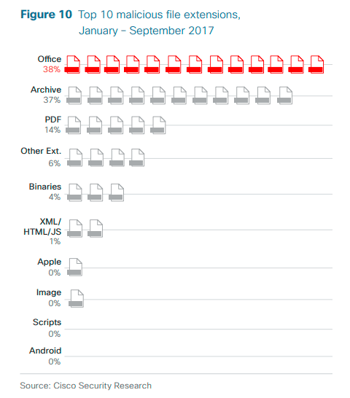 What This Means for SAP Cybersecurity
What This Means for SAP Cybersecurity
As we discovered in our own research, active content in Microsoft Office documents can be a major source of malware targeting SAP. People tend to trust MS Office documents that are uploaded to SAP (for example, a CV uploaded into an E-Recruiting application), whereas they might be more suspicious of a similar file sent via email.
Unfortunately, because SAP does not automatically scan these file attachments, they could easily contain macros that, as soon as the file is opened, wreak havoc on the SAP system via malware or ransomware.
More than 4,000 ransomware attacks occur every day. (FBI)
What This Means for SAP Cybersecurity
Speaking of ransomware, it’s a growing problem, particularly for any SAP user who receives external communications. The infamous ransomware Goldeneye targeted Human Resources departments with seemingly innocent job applications that, once opened, encrypted the users’ files and presented them with a ransom note. This type of attack could just as easily be leveled to any SAP user who receives external files like invoices, bills of lading, job orders, quotes, contracts, and more.
Imagine a manufacturer whose Production Manager just had all his files encrypted because he inadvertently opened an request for proposal that contained ransomware, and you can begin to grasp the enormity of the risk.
Thirty-one percent of organizations have experienced cyberattacks on operational technology infrastructure. (Cisco)
What This Means for SAP Cybersecurity
An increasingly connected workplace means an increased risk surface. Symantec reported in 2017 that IoT attacks were up by 600%, as cyberattackers take advantage of the vulnerability of networked infrastructure technology, such as equipment and vehicles. Because many organizations using SAP systems have this type of technology, they must be increasingly vigilant about protecting these weak links.
While SAP cybersecurity continues to evade the radar of most analyses of the cybersecurity landscape, it’s one that is not evading the attention of cybercriminals. In the 2018 Onapsis/Digital Shadows report, researchers observed a 160% increase from 2016 to 2017 in dark-web interest around ERP-specific vulnerabilities.
For that reason, it’s vitally important for SAP managers and information security managers alike to be aware of how cybersecurity trends will affect SAP, and what processes and solutions they can use to protect this mission-critical system.


Share this on social: