Considering how SAP systems are often interlinked with critical financial data, human resources records, and even vital infrastructure, a cyberattack could be devastating.

Jul 12, '17 by Joerg Schneider-Simon
Sharing files is a common part of any company’s day. Documents are shared between departments, invoices are sent from suppliers, and resumes are sent from candidates. Departments such as Accounts Receivable, HR, Procurement, and more all handle...

May 9, '17 by Joerg Schneider-Simon
Directory traversals are one of the most common SAP cybersecurity attacks, accounting for 20% of the security notes published by SAP. In these attacks, cybercriminals gain unwanted access to sensitive files or system directories, potentially...
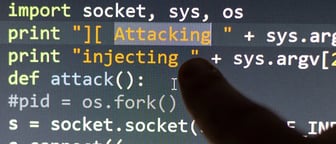
Apr 13, '17 by Joerg Schneider-Simon
External cybersecurity threats pose a very real risk to SAP systems of all sizes. One of the most common vehicles for hackers is the injection attack – both SQL injections and OS command injections. Preventing these attacks requires proactive...

Mar 15, '17 by Joerg Schneider-Simon
If you’re a manager tasked with SAP security, it’s likely that you spend a significant amount of time focused on internal and process-based security threats. However, you may be unaware of the external cybersecurity threats that can put your...

Feb 21, '17 by Joerg Schneider-Simon
In years past, corporate IT departments exerted complete control over who used their SAP applications. Any endpoint that accessed SAP was known and secured. As a result, managers tasked with SAP security were concerned about internal business- and...

Jan 25, '17 by Joerg Schneider-Simon
Many users safely employ macros to streamline repetitive processes. Unfortunately, many cybercriminals also use macros to hide malicious code in an attempt to steal information or money.
After several quiet years, macro malware is experiencing a...



